Staying ahead of threats requires constant preparation and adaptability. Cybersecurity online training offers an efficient way to equip teams with the skills to detect, respond to, and mitigate real-world threats. Through virtual training solutions, businesses gain access to practical, interactive modules that simulate scenarios employees might encounter, enabling them to develop critical skills in a controlled environment.
With rising incidents of sophisticated cyberattacks, companies must invest in training solutions focusing on relevant, up-to-date practices. Virtual training solutions deliver targeted, practical exercises, allowing teams to build strong, hands-on experience without disrupting daily operations. Unlike traditional training, which often lacks the adaptability needed for the fast-evolving cybersecurity field, online training emphasizes active learning, ensuring that employees retain knowledge and stay engaged.
Choosing cybersecurity online training as part of a company’s security strategy means providing employees with the tools to safeguard digital assets and understand emerging threats. The right virtual training solutions empower teams to take on cyber challenges confidently, minimizing organizational risks.
Why Virtual Cybersecurity Training is a Game-Changer
Virtual cybersecurity training online allows companies to tackle the complexity of modern threats with adaptable, hands-on learning experiences. With advancements in simulation technology, training providers, including virtual reality training companies, have developed specialized programs that engage learners through realistic and interactive sessions.
Virtual cybersecurity programs simulate real-life attack scenarios, allowing employees to build relevant skills in a secure environment. Effective training ensures that teams are better prepared, minimizing risks and maximizing response efficiency.
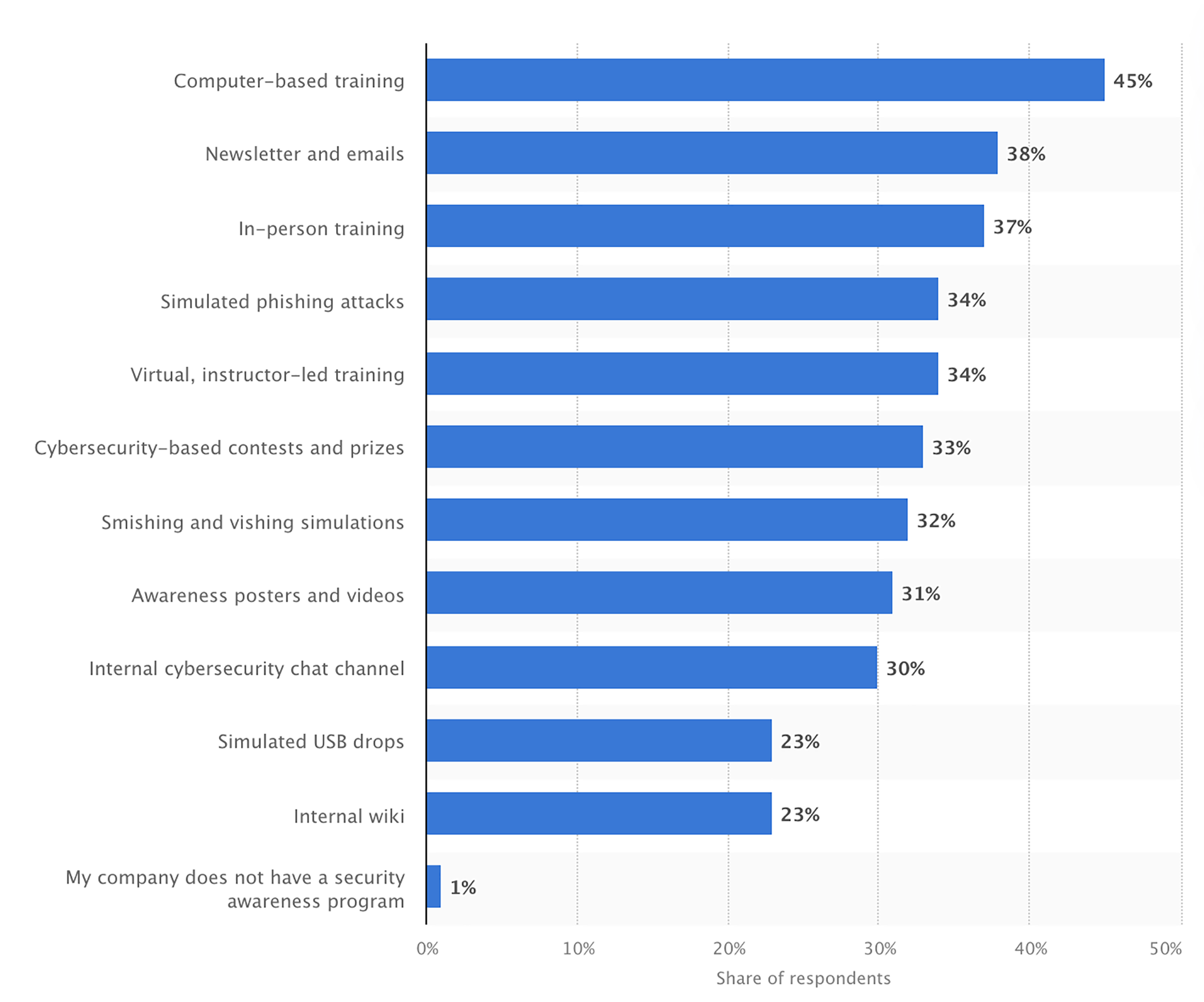
Attendance of cybersecurity training by employees worldwide in 2024, by type
Addressing Modern Threats in a Digital-First World
The rapid increase in digital threats calls for online cybersecurity training that stays up-to-date with new risks. Incorporating VR app development into training environments enhances learning by creating immersive simulations. In these digital-first scenarios, employees can practice their responses to cyberattacks without exposing the company to any actual risk.
Businesses must address threats such as phishing schemes, ransomware attacks, and unauthorized data access. Practical virtual training allows companies to cover the following:
- Simulated phishing attacks. Employees learn to recognize suspicious emails and links, building awareness and resilience.
- Incident response practice. Teams can practice rapid responses to various cyberattacks, understanding each step to limit damage.
- Data security protocols. Specific scenarios teach employees to safeguard sensitive data and manage unauthorized access attempts.
In a secure virtual environment, team members gain direct experience with cybersecurity incidents, which supports proactive defenses and improves reaction times across the organization.
Key Advantages of Cybersecurity Online Training
Cybersecurity online training provides businesses with a flexible and efficient way to improve their defenses. By incorporating VR soft skills training, companies enhance employee engagement and knowledge retention. Some key advantages of this approach include:
- Improved retention. Practical, interactive sessions help employees remember training details longer, strengthening skills over time.
- Cost efficiency. Virtual programs eliminate travel expenses and allow training from any location, making it budget-friendly.
- Customization options. Companies can tailor scenarios to fit specific needs, creating a more relevant learning experience.
- Risk-free practice. Teams can safely experience cybersecurity incidents and learning without any real risk to the company.
Embracing these benefits strengthens cybersecurity readiness across all levels, empowering teams to act confidently and reduce vulnerabilities. By integrating such tailored, interactive training, companies foster a safer digital environment that aligns with their unique security needs.
Aligning Training with Business-Specific Security Needs
Customizing cybersecurity training to address the unique needs of a business ensures that employees receive relevant, impactful instruction. Each organization faces its own set of security challenges based on factors like industry regulations, technology stack, and operational priorities. Effective virtual training allows companies to align training content with these specific requirements, enhancing preparedness and response capabilities.
For example, a healthcare organization may focus on data privacy to comply with strict regulations, while a financial institution might emphasize preventing fraud and securing transactions. Tailored training programs can include specific modules that reflect these high-priority areas.
Such an approach equips employees with relevant skills to their roles, reducing risks related to common and industry-specific threats. By focusing on precise training needs, organizations create a more resilient security structure that actively addresses their most pressing vulnerabilities.
Core Components of Effective Cybersecurity Online Training
Applicable cybersecurity training incorporates critical components to maximize learning and practical skills. Online training programs focusing on interactive scenarios, realistic simulations, and role-specific modules give employees comprehensive practice in identifying, mitigating, and responding to threats. You can choose between multiple types of simulation training to create impactful training experiences for your teams.
Interactive Scenarios for Real-World Threats
Engaging employees through interactive scenarios prepares them to handle actual cybersecurity threats confidently. Each exercise replicates a common threat or potential vulnerability, building readiness and familiarity in a controlled setting.
Phishing recognition exercises. Employees practice identifying suspicious emails, strengthening their ability to avoid phishing attempts that target sensitive data and credentials.
Malware detection scenarios. Simulations guide participants through detecting, quarantining, and resolving malware threats, essential for protecting systems from widespread harm.
Unauthorized access simulations. Employees respond to scenarios involving attempted access by unauthorized users, refining their vigilance and response to access-related risks.
Coordinated crisis response drills. Teams rehearse response actions for large-scale incidents, improving communication and efficiency, which are critical for effective threat management.
Training through such scenarios provides employees with practical experience, reinforcing their skills in identifying and responding to threats. With focused practice, teams build confidence and competence, becoming more adept at managing risks across various situations.
Engaging Simulations for Decision-Making Skills
Decision-making simulations equip employees with essential skills for real-time responses to cybersecurity threats. By engaging in simulated exercises, team members understand the choices and actions that mitigate damage and protect assets.
Incident escalation training. Employees learn to identify when an incident requires higher-level intervention, refining their judgment on when to escalate issues for prompt attention.
Strategic response selection. Scenarios require employees to choose suitable response methods for various threats, aligning their actions with best practices and standard operating procedures.
Collaborative decision-making exercises. Simulated team scenarios improve communication and coordination, fostering a unified approach to tackling threats.
Critical assessment drills. Exercises help employees assess threat levels and evaluate response options, enhancing confidence in making informed, timely decisions under pressure.
Through realistic decision-making simulations, employees become skilled in quick analysis and strategic response, which is essential for maintaining robust cybersecurity. The ability to make informed choices grounded in real-world applications significantly strengthens the organization’s resilience against cyber incidents.
Haiku – Cybersecurity Training Game

Discover how Program-Ace collaborated on World of Haiku, creating an interactive game that educates users on cybersecurity basics. From optimizing UI to enhancing game performance, our developers ensured an engaging, user-friendly experience.
Virtual Cybersecurity Training — Integrating AI and Analytics
Integrating AI and analytics within cybersecurity training programs equips teams with advanced tools to counter emerging threats. AI-powered virtual training allows organizations to simulate complex attack scenarios while using analytics to evaluate performance and provide data-driven feedback. This approach ensures that training remains adaptive and that employees continuously improve their skills based on real-world insights.
Using AI to Detect and Respond to Emerging Threats
AI-driven training programs enhance cybersecurity readiness by simulating sophisticated threats and offering realistic response scenarios. Unlike traditional training methods, AI integration allows for the simulation of highly adaptive attack patterns, providing employees with experiences that mirror rapidly changing cyber risks.
- Dynamic threat detection simulations. AI-powered scenarios enable employees to practice recognizing evolving attack techniques and building awareness of complex threats like polymorphic malware or zero-day vulnerabilities.
- Automated response assessment. AI algorithms assess employees' responses in real time, offering immediate feedback on accuracy, timing, and effectiveness, which improves decision-making skills.
- Adaptive challenge levels. AI adjusts the difficulty of each scenario based on the participant’s performance, ensuring a personalized experience that strengthens weak areas and reinforces strengths.
- Predictive threat modeling. Using AI, organizations can simulate potential future threats, preparing employees for incidents before they occur and refining strategies for faster detection and response.
AI-enabled simulations provide a valuable training layer, helping employees anticipate, identify, and neutralize threats with increasing precision. Such a technology-driven approach accelerates skill development and prepares teams for the ever-evolving nature of cyber threats, contributing to more robust overall defenses.
Analytics-Driven Insights for Continuous Improvement
Analytics-based feedback within cybersecurity training programs supports continuous improvement by identifying skill gaps and tracking progress. Organizations use these insights to tailor training, ensuring every session adds tangible value to employees’ knowledge and readiness.
- Performance tracking metrics. Analytics capture vital metrics, such as response time, accuracy, and threat identification rates, providing clear indicators of each participant's strengths and areas for improvement.
- Trend analysis for targeted training. Organizations can identify recurring weak points by analyzing trends across sessions, allowing trainers to develop targeted exercises that address specific challenges.
- Skill progression monitoring. Data-driven insights reveal how employees' skills develop over time, enabling trainers to adjust training intensity and complexity as participants grow more proficient.
- Feedback for iterative learning. Analytics offer detailed feedback for each scenario, encouraging employees to reflect on their performance and refine their skills through consistent practice and iteration.
Analytics-driven training ensures cybersecurity programs remain agile and responsive to employee needs, maximizing skill growth and readiness. As a result, organizations benefit from a workforce that understands cybersecurity fundamentals and excels in applying them across complex and varied situations.
Key Skills Developed Through Virtual Cybersecurity Training
Virtual cybersecurity training builds essential skills that prepare employees for real-world challenges. By focusing on interactive, scenario-based learning, virtual corporate training enhances threat detection, mitigation, and team coordination capabilities. These competencies are critical to maintaining a robust cybersecurity posture, enabling employees to respond confidently and effectively to cyber incidents.
Identifying and Mitigating Threats in Real Time
Training that emphasizes real-time threat detection and mitigation enables employees to develop crucial response skills. Virtual simulations guide participants through identifying suspicious activity, assessing threat severity, and taking immediate action to contain risks.
Highlight interactive elements.Threat identification exercises. Employees engage in scenarios that replicate potential threats, such as suspicious network activity or unusual login attempts, allowing them to sharpen their detection skills.- Risk assessment training. Participants learn to evaluate threat severity, determining which incidents require immediate response versus those that need monitoring, ensuring efficient allocation of resources.
- Mitigation strategy practice. Scenarios include steps for isolating threats and applying mitigation measures, reinforcing effective containment practices that prevent the spread of an attack.
- Real-time response simulations. Employees experience the pressures of live cyber threats, practicing swift and strategic actions that minimize damage and protect critical data.
Participating in this practical exercise helps students hone their abilities in rapid threat assessment and immediate action. Employees improve the company's capacity to avoid security breaches and lessen the effect of incidents by becoming experts in these tactics.
Strengthening Team Coordination for Incident Response
Effective cybersecurity relies on seamless coordination among team members, especially during incidents that require swift, collective action. Virtual corporate training provides a practical setting for employees to enhance collaboration skills essential for incident response.
In a controlled environment, participants engage in group exercises that simulate real-life cyber threats, helping them understand how to communicate effectively and execute coordinated actions. Through these sessions, employees practice working under pressure and learning to share critical information rapidly and accurately, which is essential for containing and neutralizing threats.
Virtual simulations also allow employees to experience role-specific tasks within a team, gaining insights into how each function supports the overall response. By understanding these interdependencies, participants become better prepared to step into their roles and cooperate with others, knowing how each action contributes to the larger effort. Cross-functional drills encourage employees from various departments to work together, broadening their understanding of incident management and building trust across teams.
Practicing crisis communication adds another layer of preparedness as employees learn to manage both internal and external information flow during an incident. By focusing on these key aspects of coordination, virtual training enables employees to respond to cyber threats as a united front, ensuring that every team member understands their role and contributes to a fast, organized response. The result is a cohesive and well-prepared team capable of handling cybersecurity incidents confidently and efficiently, strengthening the organization’s overall resilience.
Choosing the Right Cybersecurity Online Training Program
Selecting an effective cybersecurity online training program involves careful consideration of your organization’s unique needs and objectives. A well-designed program should offer comprehensive instruction and adapt to the evolving demands of cybersecurity.
Incorporating virtual reality training design and development enables companies to provide immersive experiences that enhance retention and engagement. The right program addresses current cybersecurity challenges while equipping teams with essential skills, making it a crucial part of a robust security strategy.
Factors to Consider: Flexibility, Scalability, and Customization
Choosing the right training program requires a focus on flexibility, scalability, and customization to ensure it aligns with your organization’s needs. Each factor plays a key role in adapting the program to your team and business objectives.
- Flexibility for diverse learning needs. A flexible program allows employees to learn independently and access materials on their preferred devices, accommodating varied schedules and skill levels.
- Scalability for growing teams. As the organization expands, a scalable program provides training that adjusts seamlessly, allowing new employees to integrate without added complexity.
- Customization to match industry requirements. Programs with customizable modules enable companies to focus on specific skills or risks unique to their sector, making the training directly relevant and practical.
- Interactive options for enhanced engagement. Programs offering VR components or simulations increase engagement and retention, making training more practical and memorable.
- Cost-effectiveness for budgeting needs. Programs that provide a balance of features and affordability allow organizations to enhance cybersecurity preparedness without straining resources.
A cybersecurity training program designed with flexibility, scalability, and customization in mind provides long-term value, growing with the organization and adapting to new challenges over time.
Evaluating Training Providers for Maximum Impact
Selecting the right training provider involves assessing their expertise, instructional quality, and ability to meet your organization’s cybersecurity goals. A high-impact provider offers a comprehensive, engaging program that enhances skills and prepares employees for real-world threats. Certain factors stand out when evaluating providers.
- Proven industry expertise. Providers with experience in cybersecurity bring insights into emerging threats and best practices, ensuring relevant and practical instruction.
- Commitment to quality in program design. A well-structured curriculum emphasizes interactive learning, making complex concepts easier to understand and apply.
- Technology-driven solutions. Programs integrating VR or AI-based components create realistic training scenarios that simulate real-life challenges, enhancing skill development.
- Ongoing support and updates. Providers who offer continuous support and regularly update content keep the training relevant, ensuring employees stay prepared for evolving cyber threats.
- Engagement in cybersecurity initiatives. Participation in industry events like the Cybersecurity Talks, which Program-Ace participated in, reflects a provider’s commitment to staying at the forefront of cybersecurity advancements.
Choosing a provider aligned with these factors enables your organization to maximize the benefits of cybersecurity training. A partner with industry expertise and commitment to innovative methods ensures the training meets current standards and equips your team for future challenges.
Program-Ace as Your Go-to Cybersecurity Online Training Provider
Program-Ace provides effective cybersecurity online training that combines advanced technology with practical, customizable solutions. As an experienced innovative solutions integrator and custom software development company, Program-Ace offers virtual training programs incorporating simulation, VR, and AI-driven elements to create realistic, hands-on training experiences.
The Program-Ace approach emphasizes flexibility, enabling organizations to adjust training to fit their unique objectives, team size, and preferred learning pace. With a focus on up-to-date cybersecurity training design and development, Program-Ace ensures that programs remain aligned with the latest threat landscapes and security practices.
Program-Ace offers adaptable solutions rooted in practical, real-world applications for companies seeking a robust approach to cybersecurity readiness. To learn more about our training options, contact us today.

























